We tend to talk a lot about security through obscurity. But what about security through virtualization?
I’ve been thinking about both security and virtualization quite a bit lately. I also had the privilege of visiting VMware‘s HQ in Palo Alto with Tech Field Day twice last year. That’s interesting because VMware is using their place as the virtualization layer between infrastructure and applications as a secure control point to reduce attack surfaces. But before we dig into that, we need to zoom out a bit and take in some needed context.
Virtual Networks
I’ve seen the future of networking and it’s virtual. Of course, so’s the past. That’s kind of what the whole OSI model thing was trying to help us with. And it’s why basically every network engineer has practice drawing physical AND logical diagrams.
What’s actually new is the growing levels of abstraction and automation.
Business Fabrics
What’s also new is the drastically increasing relevance of technological infrastructure to organizations of all sizes and shapes. As early as 2011 Forbes had declared that every company is a software company. More recently, Thompson Reuters stated that all companies are technology companies. And the trend of executives working to raise their organizations’ digital quotient to succeed during this digital revolution shows no signs of slowing down.
But what the heck does ‘going digital’ have to do with virtual networks?
As rapidly as technology is evolving, there appears to be one immutable constant. That universal need is connectivity. The network is the most fundamental layer of any infrastructure and that’s simply not changing.
The demands placed upon that network and the scale of its importance to the mission of your organization, however, are changing. Now we need more than a collection of devices that forward frames. Even more than a collection of networks that connect to each other. We need a network platform that connects all the things and is easy to manage.
When you combine a ubiquitous network fabric with identity and policy controls and then layer on consistent device and application controls, you approach the nirvana of a true business fabric. A holistic technology platform upon which to conduct your business. Well, mostly. For this to really work, you need visibility and control.
On Visibility & Control
Automation and abstraction are hot right now. That’s why everything is “Software Defined” these days. You’ve got SD dash network, WAN, security, perimeter… Heck, even the whole data center can be software defined.
But why?
What are we really talking about when we throw out terms like virtualization and abstraction or disaggregation and automation? Why do we want everything software defined?
It’s all about visibility and control.
We want to put things into the infrastructure (provisioning/control) and get things out of the infrastructure (telemetry/visibility). And we want to do this as efficiently and effectively as possible. In other words, I shouldn’t have to manually log into multiple devices to find out what VLAN is provisioned, nor to provision it when we find that it’s missing.
We also want: Control over what hardware and software we use in our infrastructure. Visibility into where all of our workloads currently live across all of our pods and clouds. Control of who can change what, anywhere in the infrastructure. Visibility of policy and intent violations that occur anywhere across the organization.
Virtually Secure
All of this visibility and control across a cohesive business fabric does wonders for our security posture.
Imagine having a single, virtual network that connects all of your applications and all of your users – no matter where they live physically. Now imagine that within this virtual network you have full visibility of all those endpoints plus complete control over how they connect.
This is security through virtualization. Embed security into the network. Embed the network into the cloud. Leverage network virtualization to push security functions closer to the applications they protect. Use connectivity to enforce policy… You get it.
It’s a powerful vision that only a couple companies seem poised to really deliver on. I’ve written previously about Juniper’s approach, which they are now calling “Secure Automated Multicloud.” Their advantage, of course, is that they are a networking company with a ton of domain expertise gained over many years. But what about VMware?
Virtualizing for Security
VMware’s obvious advantage when it comes to building a secure business fabric is their unique position as the virtualization layer across compute and mobile. They own the software that sits between infrastructure and applications in the datacenter. And with Workspace ONE (which replaced Airwatch) they own the software that sits between users and applications on our personal devices as well.
By being the abstraction layer itself, VMware can provide exceptional visibility and control almost by default. This is obviously not lost on them as they have been building a suite of products to capitalize:
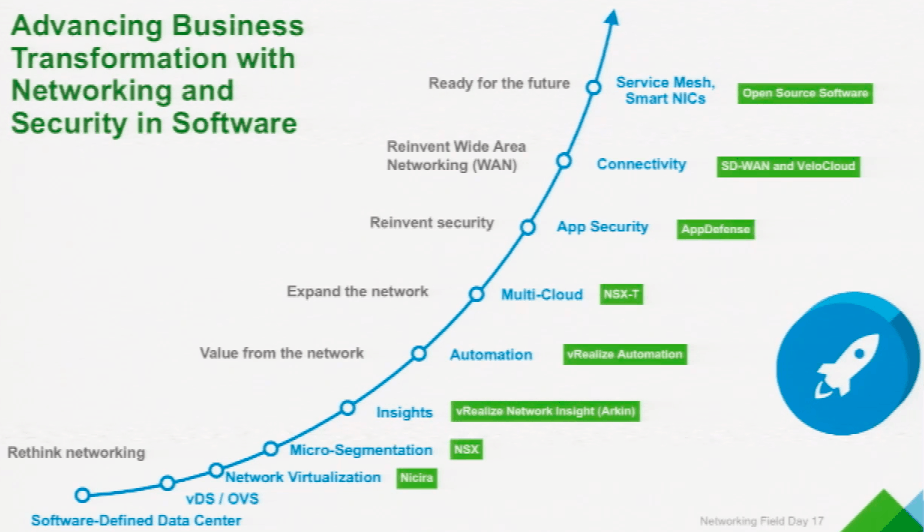
Digging In
As I mentioned above, I got to see VMware present on their vision for security though virtualization twice last year. The first was at Network Field Day 17 back in January. The follow up was at the very first Security Field Day just last month. Nice bookends for 2018!
Now it’s your turn to dig into the videos from those events (at the links right above) to get a deeper understanding of why I’m so excited about VMware right now.





[…] Security through Virtualization (brought to you by VMware) […]
[…] did it for the same reason that they embraced AWS and Terraform and multi-cloud security and et cetera. Because they know that they can’t rest on their laurels. That they must meet […]