One of my favorite quotes is from William Gibson:
The future is already here — it’s just not very evenly distributed.
I like it for a lot of reasons, not the least of which is how useful it is when thinking about the application of technology to solve business challenges. I have found countless examples of this uneven distribution when helping clients solve real world problems. Often the technology you need is already being successfully applied elsewhere.
Sometimes I describe it as “trickle down” technology. No, I’m not referring to supply-side economics. I’m talking about the ability for large companies or start-ups to innovate and for others to gain from the fruits of these innovations. They trickle down from the original users to the rest of us.
Kubernetes is a great recent example. Originally developed by Google as an internal cluster management system called Borg it is now quickly becoming the de facto standard for container management and orchestration.
Identity Security
I recently opined, over on Forbes.com, that:
The number one thing you can do to protect your organization in today’s world of cloud services and remote employees is to have a rock-solid identity security solution. This should include identity and access management (IAM), single sign on (SSO), multi-factor authentication (MFA), privileged account management (PAM) and cloud access security broker (CASB) functionality.
What’s interesting is how few CIOs and CISOs have truly invested in identity security, and specifically in PAM.
Privileged Account Management
From what I can tell, a big part of this lack of investment is due to a lack of awareness among IT professionals. Just in case you fall into that category, here’s a quick description of PAM that I penned for the OrangeMatter blog a couple months back:
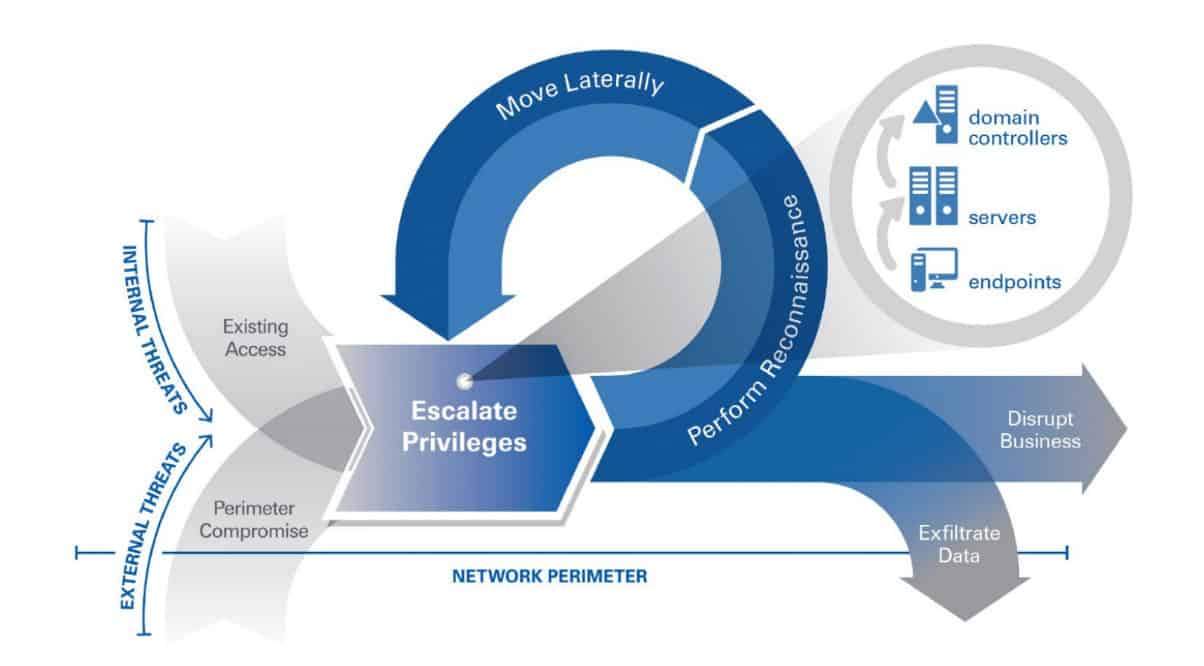
Not all users are created equal. A privileged user is one who has administrative or root access to critical systems. Privileged account management (PAM) solutions provide the tools you need to secure critical assets while allowing needed access and maintaining compliance. Current PAM solutions follow “least access required” guidelines and adhere to separation-of-responsibilities best practices.
More than that, PAM is a great way to slow or even stop lateral movement within your environment once a breach has occurred. Privileged accounts are gold for those that seek to infiltrate your company and exfiltrate your information. Better controls over these accounts make it much harder for attackers to successfully carry out their nefarious acts.
Trickle Down PAM
Okay, great, now we all have a basic understanding of what PAM is and how important it is as part of a comprehensive identity security program. But what does that have to do with a Google project and a Sci-Fi author?
Enter CyberArk.
CyberArk is a company that was founded to tackle secrets management way back in 1999. That’s ages ago in IT time. Since then, they have deployed privileged access security solutions for over 4,200 companies. This includes half of the Fortune 500 and 30% of the Fortune 2000.
For nearly 20 years CyberArk has been hard at work helping some of the worlds largest companies protect their most critical and high-value assets with privileged access management solutions. All the while, most of us were busy installing firewalls and anti-virus suites.
Fast forward to 2019. The world has changed. Smart phones and cloud services are destroying the idea of a network perimeter. Now more than ever, users and applications are the edges of our networks. Identity is the new perimeter.
And how do we define identity? In many cases it’s with secrets. Call them credentials if you like. Either way, we need to protect them. We especially need to protect the secrets that guard privileged access.
Those of us just waking up to this reality are lucky. We can borrow techniques from those that have already solved this challenge. Let PAM trickle down to our organizations. And distribute the future a bit more evenly.
CyberArk
As I mentioned above, CyberArk has been doing this a long while. During that time their offerings have expanded. Want to learn more about what they do and why they do it? Awesome – check out this great presentation by Brandon Traffanstedt:
If you think that’s interesting, you can dig into the rest of Brandon’s presentations and demos from Security Field Day here.
You can also get a deeper analysis of CyberArk from my friend Jeff Wilson on his blog here.
And don’t forget to keep your secrets safe – especially the privileged ones!
Oh, one last thing before you go – if you enjoyed reading this, I invite you to leave a comment below, share this post with colleagues, and check out some of my other security related content.