I have spent the past 18-24 months deep inside the rabbit hole that is Enterprise InfoSec (Information Security). Cybersecurity has always been a part of my work as an infrastructure engineer and architect. This singular focus was new though. In order to help my company, colleagues, and clients truly see the world of the 21st century through the lens of security, I had to both narrow and broaden my own perspective. Narrow in the sense that security became my paramount goal. Broad in the sense that security goes far beyond firewalls, networks, infrastructure, and even technology.
Now, as I pull my head up from that work, it’s time to share what I’ve found with a wider audience and community. Yep – that’s YOU.
Beyond the Firewall
First up is essentially a white paper covering the history and significance of cybersecurity (InfoSec). It also provides some high-level deployment advice. I call it a “Pillar Paper” because we define security as the first of four “pillars” of IT infrastructure. The others being networking, compute/storage, and WiFi/mobility. More on those in the future!
Staying focused on security, here are a few snippets from the Security Pillar Paper:
Security is likely top of mind already for any organization. Not only are attacks becoming more common, the potential damage caused by each threat is reaching catastrophic levels. A perimeter firewall and an A/V suite are no longer sufficient to protect your organization’s growing assets from the rising number of attack vectors. A sophisticated and comprehensive approach to security that touches every piece of IT infrastructure and every layer of business process is required to avoid potentially crippling loss of time, money, and data.
…
Organizations need comprehensive security strategies that are closely aligned with business goals. Security must reach far beyond the firewall. Every element in your organization needs to play a key role in securing the entire IT infrastructure. People, processes, and technology must work together to maximize effectiveness and constantly evolve.
…
Security is needed now more than ever. Our dependence on information systems is at an all-time high, and so is the onslaught of malicious activity. The cyber arms race is on, whether we like it or not, and our only choice is to stay ahead of the game by taking security beyond the firewall so that our operations can flourish and our organizations can stay out of the headlines.
Obviously this drives home the tagline “beyond the firewall.” But what does that mean? How can you take the advice in this paper and apply it in the real world?
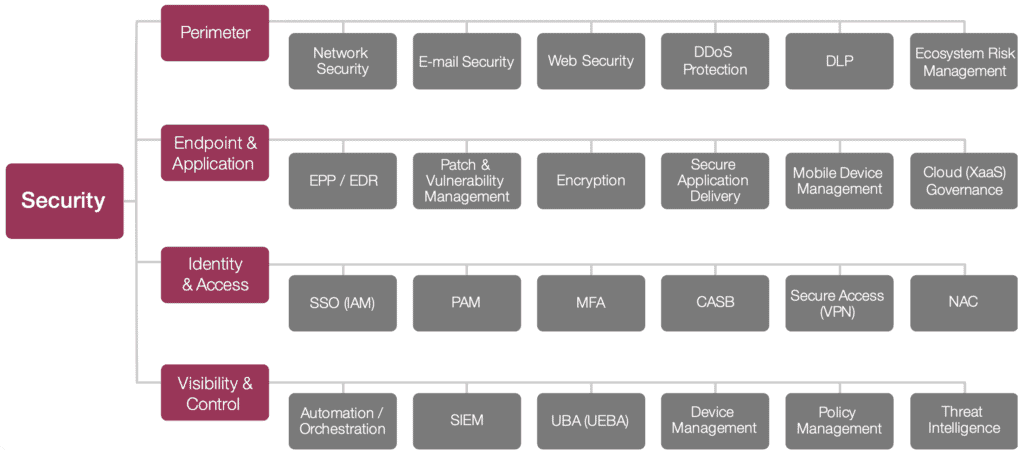
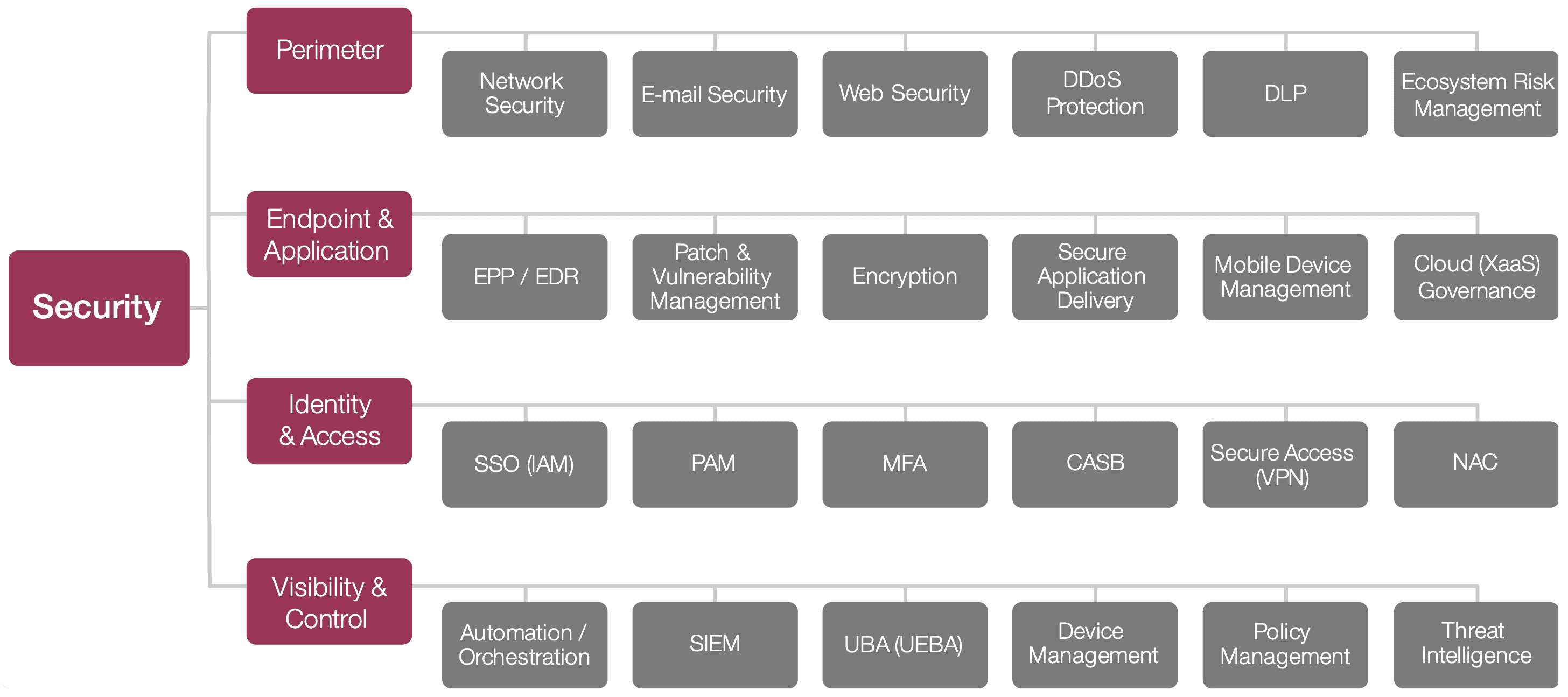
Security Reference Model
Effective cybersecurity transcends technology into the organizational, legal, and human realms. Despite that, technology is still required. Specifically the hardware, software, and services that make up your IT security infrastructure. That’s the sweet spot between “beyond the firewall” and “beyond technology” altogether.
This area is also increasingly crowded with a seemingly unstoppable wave of new products and new vendors. We want “defense in depth” not “defense in duplication” but how can we be sure? There is so much marketing buzz around so many emerging areas. It’s hard to keep it all straight.
We created a reference model of IT infrastructure security to combat this and to help us answer a few fundamental questions:
Cool chart, Chris, but what does it all mean?
More on the Model
I’ve done my best to answer that in a 6-part series over on the Orange Matter blog. For you, it probably makes the most sense to start with the last post, where I “describe how this model fits within the broader ecosystem of cybersecurity countermeasures and provide some advice on how to put it all into practice:”
https://orangematter.solarwinds.com/you-are-here-a-reference-model-for-it-infrastructure-security/
To understand the gap that this model fills I summarized some other useful cybersecurity models and frameworks in the first post of the series:
https://orangematter.solarwinds.com/you-are-here-making-sense-of-modern-infosec/
From there you can deep dive into each of the four domains and their categories in the remaining four posts:
Perimeter – Network Security, Email Security, Web Security, DDoS Protection, Data Loss Prevention, and Ecosystem Risk Management
Endpoint & Application – EPP / EDR, Patch & Vulnerability Management, Encryption, Secure Application Delivery, Mobile Device Management, and Cloud Governance
Identity & Access – SSO (IAM), Privileged Account Management, Multi-Factor Authentication, CASB, Secure Access (VPN), and Network Access Control
Visibility & Control – Automation & Orchestration, SIEM, UBA / UEBA, Device Management, Policy Management, and Threat Intelligence
In short, this security reference model provides a framework for answering three critical questions:
- Which tools provide defense in depth, and which are just causing duplication?
- How do I compare competing products and the protections they provide?
- Does my current security infrastructure provide the protection I need?
Cybersecurity Roadmap
Of course, to really answer those questions, you must look beyond technology.
Beyond technology!? What are you talking about now?
I recently heard this point confirmed by a panel of CISOs at an executive summit in NYC. All panelists agreed that the most important thing for a new CISO to learn was not any technology, tool, or technique. Their unequivocal advice was to learn the business.
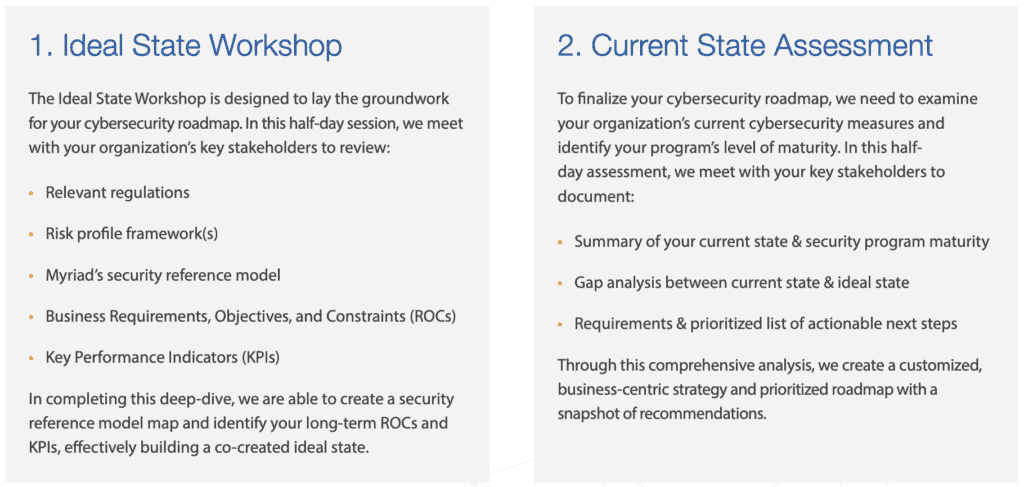
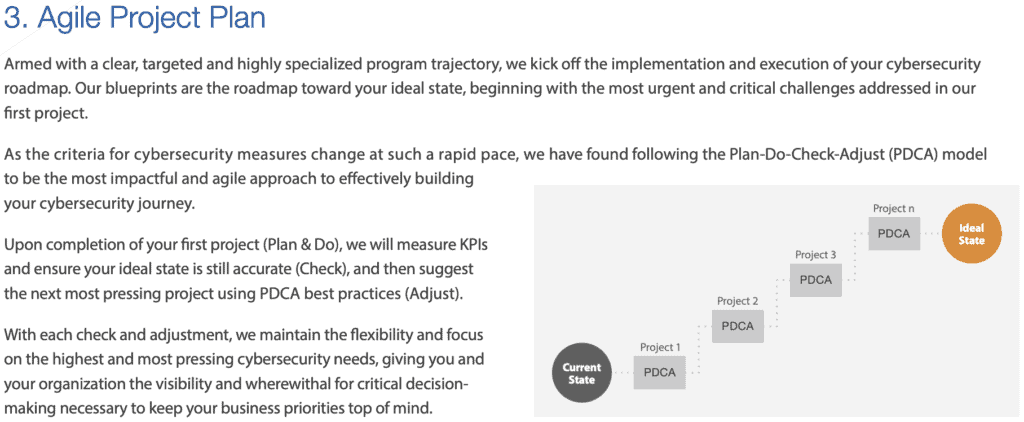
Knowing your business is a crucial part of securing your organization. It’s only one part though. You also need to know your applications, your users, your goals, and your data. Cybersecurity is a journey of constant improvement. It’s a journey that must be tailored to your organization. To guide this journey you need a roadmap. Your roadmap should clearly define the starting point (your current state), the finish line (your ideal state), and a prioritized series of steps to get you from here to there.
This is important. So, we devised a three part experience to help Myriad’s clients figure it all out:
Make Sense?
Now it’s your turn to teach me. What did I get wrong? What did I miss? What’s just not clear? How can these tools be improved?





[…] Including this cybersecurity manifesto. […]